The growth of IoT is not only appealing to academia but also to the industrial sector. Therefore, security and privacy issues for the IoT play an important role. Nowadays, cyber-attacks happen frequently, mainly due to poorly secured devices, services, and applications. This article will introduce some security methods on IoT devices, such as Cryptography Key Management, Authentication, and Authorization.
1. Cryptography Key Management for IoT
Overview Cryptography Key Management for IoT
A good cryptographic Key Management System (KMS) should be able to handle all security-related IT operations from a central location. It is a process that should be established with data protection in mind, especially with sensitive data. The use of a cryptographic Key Management System must be superior to conventional password managers.
We divided protocols into three categories: distributed, decentralized, and centralized.
- Distributed: Members of the group work together to create a shared session key.
- Decentralized: To eliminate a single point of failure, the decentralized protocols employ a hierarchy of key controllers to distribute the encryption group key to all group members.
- Centralized: To control the group and assign a group encryption key to each group member, a single entity known as the Key Distribution Center (KDC) is used.
Cryptographic models and security systems now in use are based on commonly used encryption algorithms and privacy standards.
- Asymmetric cryptography: Elliptic Curve Cryptography (ECC) and Diffie-Hellman (DH).
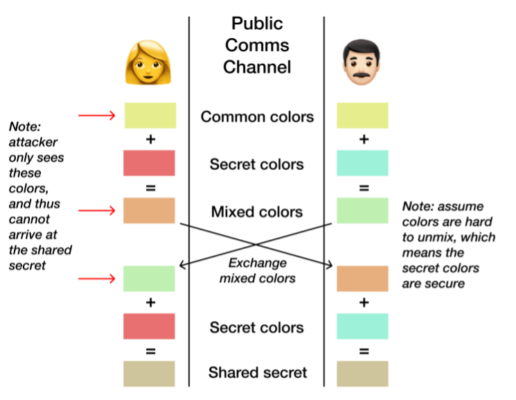
Figure 1: Diffie-Hellman (DH)
(source: Diffie-Hellman Key Exchange 🔑 ↔ 🔑 | by Matt Lim | Medium (pencilflip.medium.com))
- As secure hash functions, the SHA standards are employed.
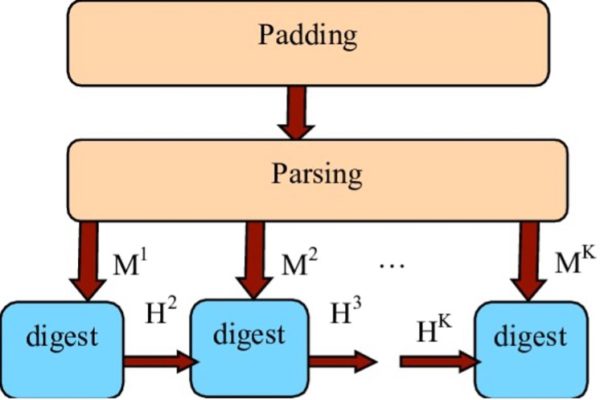
Figure 2: SHA-1 algorithm
(source: (PDF) Design of a proven correct SHA circuit (researchgate.net))
- The asymmetric algorithm RSA serves for key management, digital signatures, and asymmetric encryption.
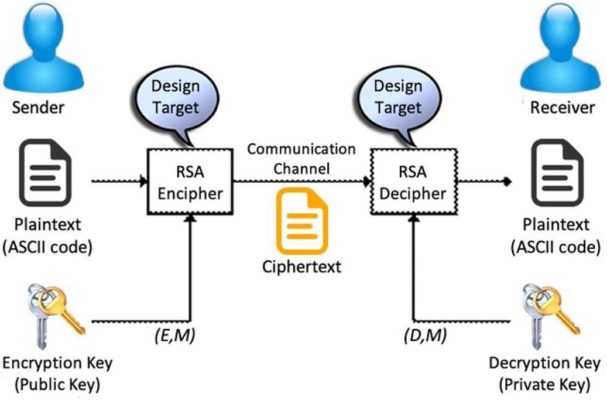
Figure 3: RSA algorithm
(source: (PDF) Secure SMS Encryption Using RSA Encryption Algorithm on Android Message Application (researchgate.net))
- Advanced Encryption Standard (AES).
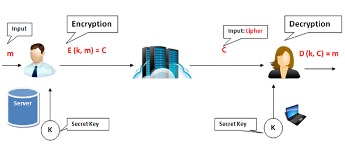
Figure 4: AES algorithm
(source: Security on the Web by Advanced Encryption Standard (AES) and Security Assertion Markup Language (SAML) – CodeProject (codeproject.com))
- Example Cryptography Key Management for IoT
- Key management protocols for group communication
Decentralized: The Decentralized Batch-based Group Key Management Protocol is an improved version of the batch-based group key management protocol that avoids a single point of failure by managing a whole network by a single entity.
- This protocol establishes a hierarchical network architecture with numerous zones, each managed by an Area Key Management Server (AKMS), and all AKMS are governed by a General Key Management Server (GKMS).
- The previous protocol’s key distribution responsibilities are now controlled by an Area Key Management Server (AKMS), with each zone’s AKMS operating independently of the other zones.
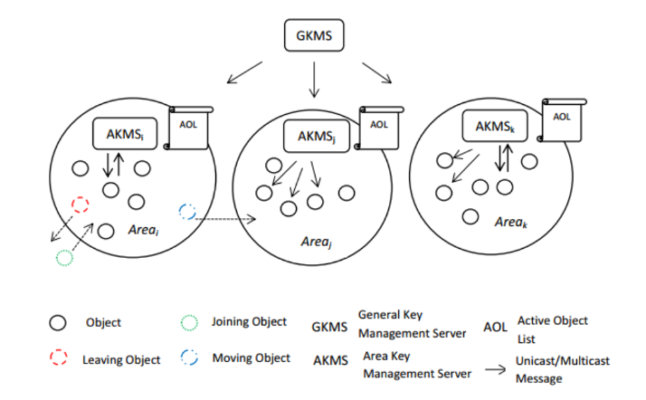
Figure 5: DBGK network model
(source: (PDF) A Decentralized Batch-based Group Key Management Protocol for Mobile Internet of Things (DBGK) (researchgate.net))
Centralized: The protocol for establishing a key for a smart home energy management system is presented. The network consists of a resource-unrestricted home controller terminal (HCT) and Zigbee nodes with minimal computational power. The HCT will serve as a security manager and will help with key provisioning on other nodes.
- Firstly, it establishes a session key with each Zigbee node using ECC.
- Secondly, it creates a group key in order to secure communication with other Zigbee nodes.
- Two-party key establishment protocols
Distributed: Distributed Key Exchange scheme for HIP-based IoT (D-HIP), offers a distributed and lightweight key exchange protocol to minimize Host Identity Protocol (HIP) computationally costly cryptographic procedures. Heavy cryptographic operations are outsourced to proxies in the vicinity, which are less constrained nodes. Each proxy takes part in the computation and transmission of a portion of the initiator’s public DH key, as well as the derivation of the common DH key prior to its construction by the initiator.
Benefits Cryptography Key Management for IoT
Security evaluation: Ensures security objectives, including authentication, integrity, confidentiality, and avoidance of 2 attacks (replay attack and Man-In-The-Middle). Keys and certificates will be managed centrally. Limit possible risks.
Group communication: An entity calculates the group key and transmits it to all members of the group so that they may interact securely.
- The connected car: Sensor nodes work together to send out safety alerts.
- E-health: Sensor nodes implanted in the patient’s body interact with one another to provide a report on the patient’s health.
- Smart home: The Zigbee nodes work together to provide a report on energy and water use. It ensures that all key management criteria are met and that the primary security objectives are met, as well as the batch-based group key management protocol that validates all security objectives.
Two-party communication: does not need a lot of calculations or a lot of energy. There are many benefits to IoT, such as:
- E-health: the exchange of data between a sensor node and a server.
- Smart parking: a message is sent to the user’s smartphone informing him that a pallet is available nearby.
- Smart home: the user’s smartphone receives a notice from the refrigerator informing him of the missing foods.
- Smart shopping: a solid relationship with the customer To introduce himself, he used his smartphone.
Future of Cryptography Key Management for IoT
Keys are used to securing smart IoT devices (OMS).
Strict adherence to data protection procedures for IoT devices. For example, in Europe, subject to the European Data Protection Regulation (GDPR).
Use asymmetrical or symmetrical encryption with one or more private keys for each IoT device. Until each IoT device achieves certain reliability, it will be connected to a common network.
It is important to understand the requirements of an IoT application before designing a security solution.
Improve the 2 characteristic factors of each IoT device: size and heterogeneity.
When using Cryptography Key Management for IoT needs to make sure to do it within IoT-specific resources (memory, power supply).
2. Authentication and Authorization for IoT
Introduction Authentication and Authorization for IoT
Authentication is the act of identifying a device, whereas authorization is the process of granting permission. These procedures are used by IoT devices to provide role-based access control and guarantee that devices have just the access and permissions they require. Only authorized devices can interact with other devices, gateways, cloud accounts, and applications.
To assign and verify device IDs, use public key infrastructure (PKI) to link devices with public key certificates from certificate authorities. PKI establishes the authenticity of an IoT device on a network for data sharing.
How do models work Authentication and Authorization for IoT?
Security is divided into two groups: centralized and distributed.
- Centralized model: The authentication certificates for IoT devices are distributed and managed by a centralized server or a trusted third-party application. The certificate’s central repository performs the verification and authentication when devices join the network.
- Distributed model: Devices keep track of certificates and identities, as well as verify authorization.
There are three primary security mechanisms for IoT authentication and authorization:
- Centralized three-way authentication: An administrator pairs authentic digital certificates with the devices and registers them with a central authority or server. The secure handshake between the two devices that want to communicate is facilitated by the central authority. The security certificates aren’t stored on the devices and can’t be taken by thieves in three-way authentication, but the gadgets still offer excellent protection. Because it eliminates any authentication delay, this technique is suitable for always-connected devices or those with an on-demand internet connection.
- Distributed two-way authentication (known as mutual authentication): When both devices must authenticate each other before communicating, this protocol is employed. Each device must keep a distinct digital identity from the other devices, and then the IDs must be compared. The devices can only connect if the first device trusts the digital certificate of the second device and vice versa.
- Distributed one-way authentication: When two devices connect, the protocol requires that only one of them authenticate itself to the other, while the other is not authenticated. A password hash or a digital certificate identifies one device as valid for the other. The second device examines the password or certificate and compares it to the stored information when the first device tries to connect. The device approves the connection if the information is correct.
Benefits for Authentication and Authorization for IoT
Unauthorized users or outside devices attempting to enter the network through a targeted device are protected by strong IoT authentication.
Help users of IoT devices have confidence in the devices. In addition, they ensure the reliability of devices when connecting to each other.
Each IoT device will have its own identification code, which makes the device identification process easier. It helps to connect one device to another and also to a central server.
It also helps that when there is a breach of an IoT device, users can easily revoke the functionality or turn off the device.
It helps identify and mitigate security risks. Prevent illegal intrusion into user accounts. In particular, it helps with early detection in the early stages.
Future of Authentication and Authorization for IoT
To guarantee that only authorized devices connect to and communicate with the network, IT managers must monitor the network for machine IDs. Admins can also receive notifications if unauthorized devices attempt to connect.
IoT device security is also dependent on the communication protocol used by a network to connect and share data. This should be further developed in the future.
Message Queuing Telemetry Transport (MQTT) is a more efficient and lower footprint protocol that is fast becoming the IoT security standard. MQTT links a client to a server as a centralized method of IoT security. MQTT helps to monitor a lot of IoT devices. It also has bandwidth throttling, data transmission smoothly, and increases security between devices.
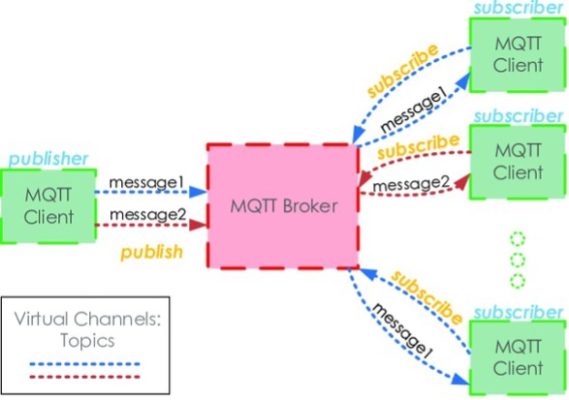 Figure 6: MQTT
Figure 6: MQTT
(source: (PDF) Access Control Mechanism for IoT Environments Based on Modelling Communication Procedures as Resources (researchgate.net))
Vocal Resonance: It may be utilized as a passive biometric and has a high level of accuracy when it comes to identifying and verifying people.
Machine learning and blockchain-based authentication: 2-factor acceptance guarantee. Firstly, IoT data is checked by other IoT devices without a centralized mechanism. Secondly, the copies of the ledger must be synced across all IoT units.
Use biometrics for Authentication and Authorization.

Figure 7: Biometrics for Authentication and Authorization
(source: Two-Factor Authentication (2FA) Explained: Biometric Authentication (identityautomation.com))
Conclusion
In the future, when the number of IoT devices becomes increasingly popular, the security requirements will be increasingly enhanced. Security is an issue that should be prioritized after the device’s function to avoid data loss and leakage. In particular, important or sensitive data. Therefore, it is necessary to improve the security of IoT devices in various ways.
Source of references:
- How to use IoT authentication and authorization for security (techtarget.com)
- (PDF) Authentication and Authorization for Mobile IoT Devices Using Biofeatures: Recent Advances and Future Trends (researchgate.net)
- (PDF) Cryptography and Security in Internet of Things (IoT): Models, Schemes, and Implementations (researchgate.net)
- (PDF) Security analysis of existing IoT key management protocols (researchgate.net)
- What is a Cryptographic Key Management System? The Security Lifecycle Solution. – MTG AG (mtg.de)
