1. Identification and Authentication Issues in IoT
The Internet of Things (IoT) provides everyday devices with the ability to identify and communicate with each other. The IoT applications are extremely versatile ranging from smart homes, smart cities to smart wearables, smart healthcare, etc. Therefore, an enormous amount of devices will be connected to collect, perform analysis and make decisions without the need for human interaction. Security is an obligatory requirement in such circumstances, and in particular authentication and identification are amongst the most important issues given the harm that could happen from malicious devices in an IoT system. The number of smart devices is growing exponentially, and so does the amount of threats the IoT systems have to face.
The requirements and limitations of the connected devices raise multiple issues, including connectivity challenges for a huge number of devices to communicate with each other and security challenges with the mission of protecting IoT networks from infiltrators and attackers. The traditional communication protocols are inefficient for IoT systems because of the resource-limited nature of IoT. Cryptographic schemes are typically designed for high power, high processing, and large memory devices. This led to the invention of authentication schemes that are lightweight and more suitable for IoT and Wireless Sensor Networks (WSN).

Source: https://ieeexplore.ieee.org/mediastore_new/IEEE/content/media/6287639/8600701/8871112/nandy15-2947723-large.gif
The major types of threats for an IoT network can be categorized as masquerade attack, man-in-the-middle attack, DoS attack, forging attack, guessing attack, physical attack, routing attack. The strategies of the attackers are extremely versatile ranging from attempting to counterfeit users’ identification, imitating an existing component in the system, snooping network traffic between devices, trying to jam communication by flooding the network with packets, and eventually penetrating the network to generating an alternative route to send or receive packets in a network.
2. Solutions
 Source: https://ieeexplore.ieee.org/mediastore_new/IEEE/content/media/6287639/8600701/8871112/nandy16-2947723-large.gif
Source: https://ieeexplore.ieee.org/mediastore_new/IEEE/content/media/6287639/8600701/8871112/nandy16-2947723-large.gif
Authenticating every single device is a challenging task to accomplish. Authentication is the process of validating users’ and devices’ identities before they can access the network or an information system. Radio Frequency Identification (RFID) can play an important role in the identification of entities. It utilizes electromagnetic induction and propagation of electromagnetic waves to distinguish various objects. Many security mechanisms have been designed and proposed including cryptographic, password-based, biometric, token-based, and multi-factor authentication.
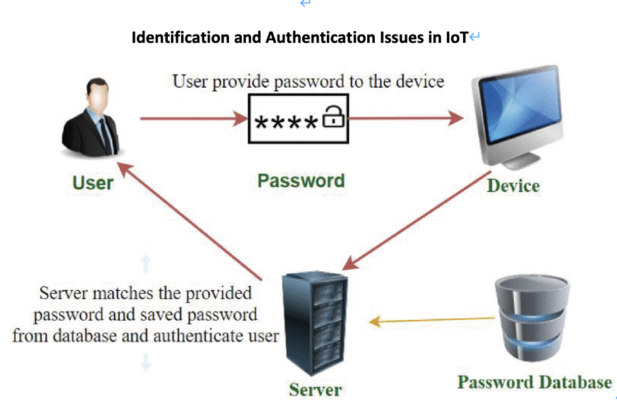
Password-based authentication is common for device or user verification. A password is a combination of letters, digits, and special characters. Users need to choose their own unique ID and password which are reserved in the database. This data can be stored in an authentication server or even in the sensor’s memory. Only when a user provides the matching ID and password can they access the system and perform desired actions.
In token-based authentication, a token is a piece of data that is generated by the server to identify a user or device. For soft token-based authentication, a one-time password (OTP) is provided by the server and forwarded to the registered device or user and a copy of the OTP is preserved in the database. The server then matches the user-provided OTP with the one in the database to authenticate the entity. On the other hand, for hard token-based authentication, a physical card or device containing information for verification is created.
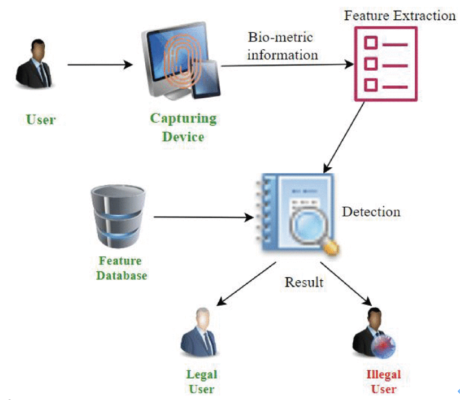
Biometric authentication is based on the biological feature of human beings. For this technique, a scanner is needed to collect unique biological data from a user and compare it with the data in the database that has been previously collected in the registration process. There can be many different ways to maintain the uniqueness of the data. A system can utilize the methods of fingerprint, face, iris, retina, hand or voice authentication, or even a combination of them.
Alternatively, due to its versatility, multi-factor authentication is getting the most interest from researchers to make the authentication process more secure and effective. Multi-factor authentication combines two or more ways to identify the user or device identity.
3. Conclusion
The current concept of network and connectivity is still in the process of being developed and may undergo major changes in the near future. The expansion of IoT and connected devices is inevitable but security on IoT will need improvements so as to provide reliability and protection for users and systems. Authentication and identification remain major challenges because there are gateways for accessing a network.
4. References
https://www.researchgate.net/publication/313574376_Security_and_privacy_issues_in_IoT
https://ieeexplore.ieee.org/abstract/document/8871112
https://res.mdpi.com/d_attachment/sensors/sensors-19-01141/article_deploy/sensors-19-01141.pdf