As technology develops, new problems also arise, one of which is cyber attacks. The web hacks or the spreading of viruses must have been heard by everyone, but have you ever come to attacks against the Internet of Things (IoT) system? IoT systems are being applied more and more in industry and households. With the amount of data in each device and the ability to control the entire production system in the industry, IoT is a good match for hackers and those with bad intentions. Today, let’s learn with Speranza and possible attack techniques in IoT so that they can be prevented.
1. What are IoT attacks?
The total number of IoT devices today is in the billions, and store huge data warehouses. Most of this data is closely related to people such as contact information, environmental and health measurements including sensitive personal data. When bad guys try to break into any device or data stream, an attack has occurred. Scenarios could be stealing or modifying data, hijacking devices or entire systems, or possibly connecting devices to other virtual networks.
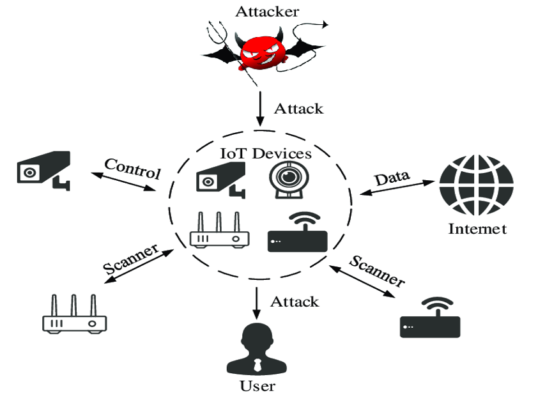
The risk of attack when the IoT system is increasingly developed
Source: https://www.researchgate.net/figure/Internet-of-Things-IoT-attack_fig1_340036543
It would be bad if an IoT system was hacked. The data in the system is mostly real-time and has a lot of impact on their owners. Imagine you are in your smart home but someone else can spy on you. Worse, you can imagine an auto production line that just needs to be wrong in the number of a part, which can lead to the failure of the entire car, or worse, cause an error that causes the entire line to stop working. Or a criminal organization hacks into the security camera system and deletes all footage of them. All of the above makes us pay more attention to security issues, especially for each device. Below are the common attack techniques used, including physical, MAC, and network attacks.
2. Physical attack
Physical attack is to interfere with the physical components of the system, here are the devices. The Internet of Things is a vast and distributed collection of devices. The devices are mostly for mechanical purposes and home electronics so everyone can access them. Their mechanism also only focuses on connectivity issues but has not invested in security. Therefore, there is a potential risk of infiltrating any point in the system and opening a serious vulnerability for hackers to take action.
Physical attacks require the attacker to be near the system. For example, sensors use AES encryption to transmit data. Hackers manually access the device and obtain the AES secret key, thereby hijacking the network and login credentials. Bad guys can also get close to the device and interfere with the chip’s electrical pulse system. Thanks to specialized devices, the chips can be modified to behave and work as they please. Hackers can even disassemble machines and embed malicious programs on the chip’s surface. Physical attack is said to be unlikely, but once it does, the consequences are unpredictable. Investing in people and strengthening hardware protection is something everyone should do, especially companies that use IoT in the industry.

The potential risk of physical attack on devices
Source: https://www.networkworld.com/article/3331676/iot-devices-proliferate-from-smart-bulbs-to-industrial-vibration-sensors.html
3. MAC attack.
I: What is MAC
MAC stands for Media Access Control, which is a link layer in the network model. MAC has the function of creating the mechanism for addressing and controlling access to the device. MAC acts as an interface that makes it easier to transfer data in an IoT device. In addition, it also allows multiple nodes to connect to the same physical environment and share that environment. MAC address, also known as physical address, is the default interface of a device. Each network-connected device has only one MAC address to identify in the system. This address is attached to the network card and specified by the manufacturer.
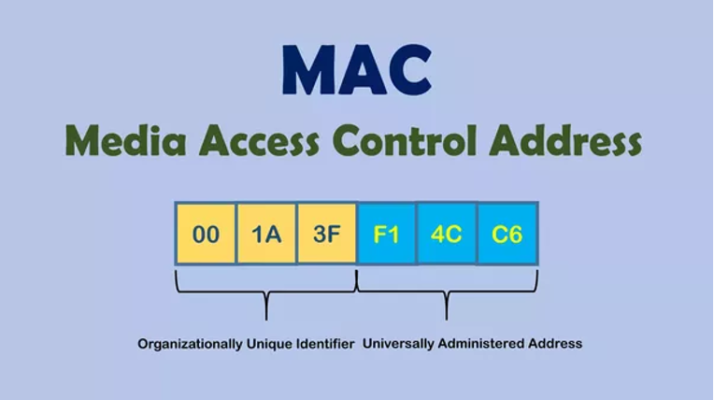
MAC address.
Source: https://bizflycloud.vn/tin-tuc/mac-address-la-gi-20181030104331099.htm
II: MAC attack and the danger
There are many types of MAC attacks. The first is MAC spoofing which is a type of attack that penetrates the system by spoofing the identity. IoT systems are very vulnerable to this. Most devices come from different manufacturers and there is no common security standard, so it is difficult to detect counterfeit devices.
The second type of MAC attack is a jamming attack. With its vast scale and data transmission over wireless networks, IoT systems are fertile ground for this type of attack. The hacker will create a base station and send a series of signals to the devices in the system. The sudden increase in traffic destroys the transmission line, causing system disruption. In more detail, this base station is considered as a node running MAC protocols and routing like a device in the system. The more stations that cause interference, the greater the impact on the network, from losing the ability to communicate between two devices to blocking the entire system.
When life depends on IoT, MAC attacks have a big impact.
Source: https://atmosphereiot.com/news/2018-12-14-iot-system-architectures-begin-with-the-data-in-mind/
III: Network attack
Everything in IoT has an Internet connection, of course hacking through the network is the hacker’s favorite way. Common types of cyberattacks with IoT are botnets, man-in-middles, or installing malware on devices.
The first is ransomware. The bad guys try to send malicious software hidden in the information to the device over the network, if the user accidentally downloads it, it will activate this software. Ransomware often locks the device to demand ransom from the user.
Another attack is a botnet, which is a form of using hijacked IoT devices to continue attacking other systems. Thanks to the malicious code installed on the device, they will create a virtual network and then perform DDoS, collect data and spy on other systems, send spam, and more.
Conclusion
Hopefully, through the article, you have a better understanding of attacks on the Internet of Things system. This is something no one wants, but it has happened, so we must always be as vigilant as possible. IoT will grow even more and security is a priority for the survival of this technology.
Reference Source
https://www.depts.ttu.edu/cs/department/seminars/abstracts/Abstract_Nahid.pdf
https://www.researchgate.net/publication/311250306_PHYMAC_layer_attack_detection_system_using_neuro-fuzzy_algorithm_for_IoT_network/link/5b0308710f7e9be94bdab94a/download
https://www.trendmicro.com/vinfo/mx/security/news/internet-of-things/the-iot-attack-surface-threats-and-security-solutions
